Globally leading security solution for the safe protection of network infrastructures
Vulnerability diagnosis and mock hacking verification solution
(Nexpose / Metasploit / AppSpider)
Solution of Rapid 7 is a product for the protection of the assets within the company by analyzing / verifying / countering the security vulnerabilities of the companies (servers, DB, network and security) in automatic format.
Background for the introduction of the product
Majority of the formats of the security accidents that have recently been on the rise rapidly are through the vulnerabilities of the internal system and software. New vulnerabilities are being discovered even at this very moment.
Although the personnel in charge of security of the company need to manage the exposure of the internal assets to such security vulnerabilities and prevent security accidents through continuous security update, it is impossible to manage the countless number of systems and applications through manual methods.
The Solution of Rapid 7 automatically detects the security vulnerabilities of the corporate assets, presents the measures to be taken in accordance with the ranking of the threat and proposes the means of the protection / management of internal assets at the minimum cost and time through verification through actual infiltration test.
-
Management of security vulnerabilities
- Investigation and identification of security vulnerabilities of IT assets
- Setting of security for vulnerability, integrated diagnosis of the threats in the domains of security control
- Automatic diagnosis according to the changes in asset environment / discovery of new vulnerability
- Automatic reporting of the improvement measures to be taken for each of the rankings of risks
- Supports Korean language
-
Web-dedicated management of vulnerabilities
- Web-dedicated analysis of security vulnerabilities
- Support latest web applications (JSON, REST, AMF, SOAP, AJAX)
- Intuitive monitoring through Coverage Map
- Management through automatic linkage with Nexpose
-
Mock penetration test
- Attack simulation for verification of vulnerability risks and status of defense
- Automatic mock penetration test
- Phishing exposure and security awareness test
- Web application penetration test
Cloud-based
-
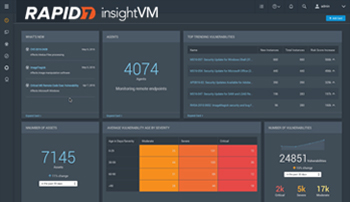
insightVM
-
Collect
보안 취약점 자동 수집, 모닝터링 및 분석
-
Prioritize
실시간 위험 확인 및 취약점 우선순위화
-
Remediate
취약점 제어 방법 제시 및 조치 현황 추적
-
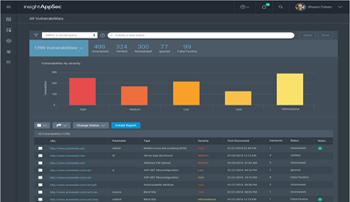
insightAppSec
-
Collect
웹 어플리케이션 취약점을 신속하고 간편하게 파악
-
Prioritize
직관적인 대시보드를 통하여 전체 웹 어플리케이션 취약점 관리
-
Remediate
공유 및 협업을 통한 수정사항을 신속하게 처리
-
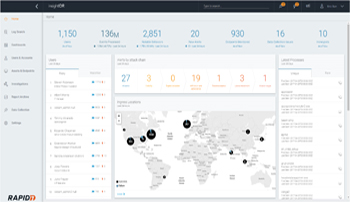
insightIDR
-
Unify
SIEM, UBA, EDR 통합 모니터링 통합
-
Detect
사용자 행위분석 공격 탐지
-
Insight
신속한 침해사고 분석 로그 분석 및 행위 가시화
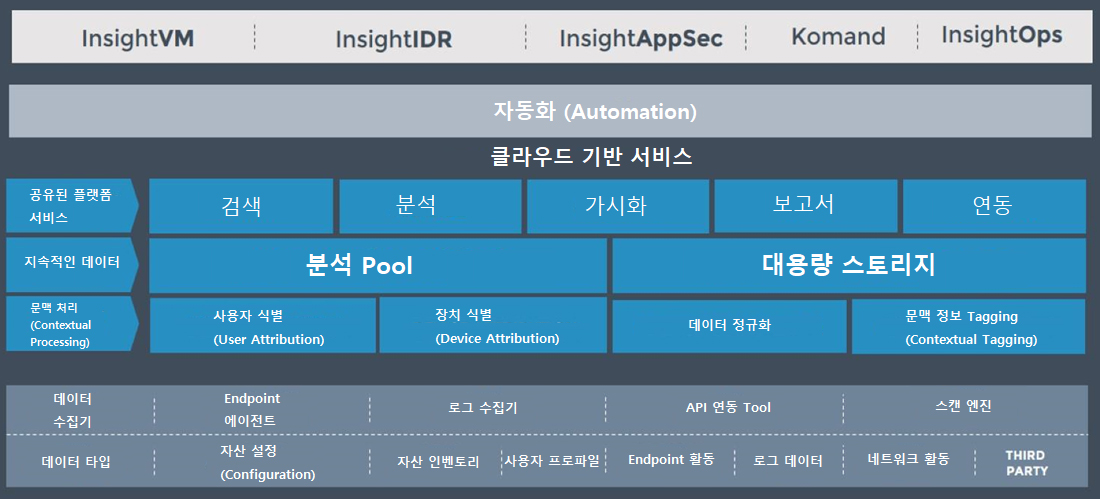
Insight Platform – IT/보안 운영자를 위한 차세대 보안 플랫폼